1 Introduction
With the advent of NFC, more and more NFC devices and applications are on the market. However, the full potential of NFC is not yet in the hands of all developers. In particular, the security element SE (secure element), a hardware-based card emulation smart card chip for security, is still under the strict control of device manufacturers and mobile operators.
At the same time, in order to interact with existing RFID systems, including access control, ticket cards and payment systems, some form of card simulation must be implemented on the NFC device. On NFC devices, security units are used to store important security applications, including credit cards, access control and public transportation applications. With the NFC controller on the device, the security unit can be used just like a regular contactless smart card.
In the field of payments, this NFC technology is the most promising place to return, and its application is currently heavily dependent on security units. Many companies want to be allowed to use security units in order to get a slice of the field. As a result, many developers have called for some simpler card emulation.
One of the methods is the software card simulation method (referred to as software SE) implemented by RIM on the BlackBerry platform. Applications on NFC phones can interact with existing RFID systems without the need for a secure unit. The first feeling of this technology is that it will bring significant progress to NFC equipment. First of all, this technology has opened the door for the majority of developers to implement the card simulation function, which was previously strictly controlled. Second, this will increase the range of NFC technology usage, resulting in an increase in demand for NFC equipment. Finally, it will drive NFC into a truly technology with a wide range of applications. However, in addition to these benefits, there are many negative issues.
This article begins with an introduction to NFC technology and its operating modes, further explaining the types of card emulation and their use in current NFC devices. Finally, based on the current application and the latest research results, this paper evaluates the advantages and disadvantages of software card simulation.
2. NFC
Near FieldCommunication (NFC) near field communication technology was first standardized by ECMA (ECMA-340, ECMA-352) and then adopted by ISO/IEC (ISO/IEC18092, ISO/IEC 21481). NFC is an advancement in inductively coupled short-range radio frequency identification (RFID) technology. Based on the ISO/IEC 14443 and FeliCa (JIS X 6319-4) standards, NFC is compatible with existing smart card systems. Recent standardization work includes compatibility with ISO/IEC 15693 proximity sensing coupling systems. In addition to standardization work, more specific data formats, protocols, interoperability, requirements, device certification and NFC applications are being promoted by the NFC Forum (http://).
A basic principle of NFC technology is "completed in one contact". This means that an easy interaction between an object or NFC device and another NFC device triggers an interaction. These objects are called NFC tags (based on RFID sensor-based contactless memory chips). These tags can store content such as Internet address URLs, phone numbers, text messages SMS or electronic business cards. Users can use the tag to contact the NFC device to obtain this information.
The NFC terminal can work in active, tempered and bidirectional modes;
1, card simulation mode, NFC simulation for a card
2, reader mode, NFC simulation for the reader, read and write the card
3, two-way data sharing mode, two NFC terminals exchange data with each other, can be used for initial verification of Bluetooth and wireless connection
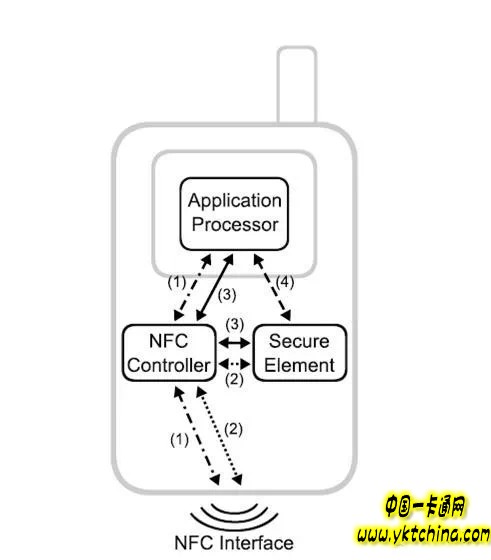
Figure 1 shows the transmission of NFC data in a medium NFC handset. The application processor is the main processing unit of the mobile phone, and the NFC controller is the core component of the NFC function in the device. It includes an NFC modem and pre-processing commands and data. The security unit is a smart card chip that enables secure hardware-based card emulation. Path 1 is the command and data flow between the application processor and the NFC controller, and the path exists in both the peer-to-peer mode, the card reader mode, and the software card emulation. Path 2 is the command and data interaction between the security unit and the NFC controller, which exists in a secure hardware-based card emulation mode. The security unit can not only interact with the outside through the NFC interface, but also with the main controller. In this way, the information in the security unit can be controlled via a mobile phone or cellular network. Path 4 indicates that the security unit is connected to the primary controller or is connected to the NFC interface via path 3. This path 2 and path 3 usually only select one of them, which means that only one of the two modes is activated at the same time.
Translator's Note: When NFC works in card emulation mode, path 1 is a software-based card emulation, ie Host Card mode. Path 2 is a hardware-based card emulation, Virtual Card mode. Paths 3, 4 represent the control of the security unit by the handset, and which path is used depends on the hardware type of the SE. The mobile phone access SE is called the WIRED CARD mode, such as when initializing or downloading an application to the SE. In WIRED CARD mode, the virtual card mode or host card mode is blocked.
2.1 card simulation
NFC card emulation can be selected in a variety of ways. The analog approach can be differentiated by communication standards, support protocol layers, support command sets, and differences in NFC device components that are specifically simulated.
For communication standards, there are three options, ISO/IEC 14443 Type A, ISO/IEC 14443 TypeB and FeliCa (JIS X 6319-4). Support for these three standards depends on the location of the NFC controller, safety unit and application. . For example, ISO/IEC 14443 Type A, ISO/IEC 14443 Type B is widely used in Europe, and FeliCa (JIS X 6319-4) is mainly used in Japan.
Another difference is the NFC device component that performs the simulation operation. On the one hand, the card simulation can be performed on the software, that is, the device application processor. On the other hand, the card simulation can be performed by a dedicated smart card chip, that is, the security unit. .
2.2 Safety unit
The security unit is a dedicated microprocessor chip on the NFC device. The chip can be integrated with an NFC controller. It can also be integrated into other smart cards/security devices in NFC devices. These integrated chips can be UICC multi-function integrated circuit cards (in most cases SIM cards) or SD secure digital memory cards.
Many security units (such as NXP's SmartMX) use standard smart card chips, including contact or contactless smart cards. Its software and hardware architecture are the same. The only difference is that they have different external interfaces. Ordinary smart cards have ISO/IEC 7816-3 (contact) or antenna (contactless) interfaces, and the security unit has a direct interface in addition to these interfaces. Connect to the NFC controller (eg NFC line interface NFC-WI, or single line protocol SWP).
The safety unit has the same high safety standards as conventional smart cards. It provides secure storage, a secure execution environment and hardware-based encryption algorithms. The security unit chip is used to read and manipulate stored data and is resistant to various attacks. Its chips, operating systems and design processes are evaluated and certified to high security standards. For example, Common Criteria protection profiles for smart card microchips. Therefore, the security unit satisfies security-related applications such as payment and access control systems.
An important unresolved security issue in smart cards is the relay attack scenario. "Relay attack" means that communication with a smart card is propagated to a relatively long distance by another carrier relay. An attacker can illegally use the victim's smart card remotely. This relay attack on contactless smart cards was first confirmed by Hancke, who achieved relay attacks through signal-layer communication between smart cards and RFID readers. Kfir and Wool significantly increase the communication distance and can easily use their smart cards without the user's knowledge. Roland etal revealed that the security unit can not only be attacked through a contactless interface, but also through software running on the mobile application processor. Anderson shows that NFC phones are ideal for relay attacks on contactless smart cards. Francis et shows that it can attack relays of NFC point-to-point communication and contactless smart card communication through an attack platform composed of Bluetooth or other wireless communication methods of two NFC mobile phones.
3. Software-based card simulation
Software card emulation is a new way to perform card emulation on NFC phones. It was first introduced by RIM on the BlackBerry platform. In addition to supporting multiple security units, the BlackBerry 7 platform supports the emulation of NFC tags and smart cards through mobile application controllers.
By specifying an NDEF message, the application can emulate NFC Forum Type 4 tags, which can be saved in a virtual tag. This type 4 tag protocol is handled automatically by the BlackBerry system. An NFC device operating in this mode can be used to exchange data with another NFC device operating in the reader mode.
Spiral Spring,Flat Spiral Spring,Spiral Torsion Spring,Spiral Tension Spring
applicaiton: viation,automotive, motorbike, bicycle, automatic equipment, household appliance, medical device ,toy, telecommunication,computer, instrument and meter,furniture, electric tools,mold and other industries
China Spiral Spring,Flat Spiral Spring supplier & manufacturer, offer low price, high quality Spiral Torsion Spring,Spiral Tension Spring, etc.
Spiral Spring,Flat Spiral Spring,Spiral Torsion Spring,Spiral Tension Spring
Shenzhen Lanejoy Technology Co.,LTD , https://www.szlanejoy.com